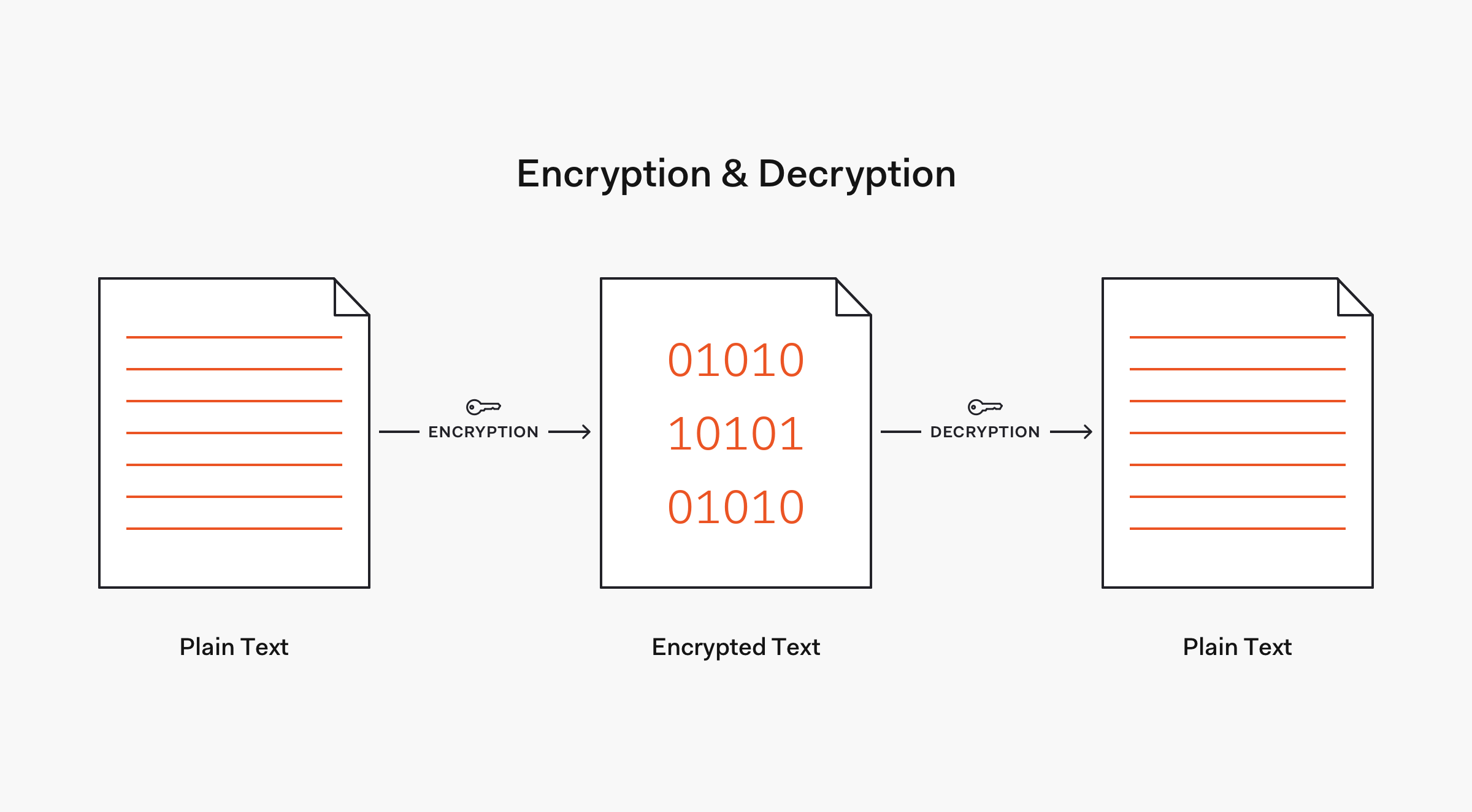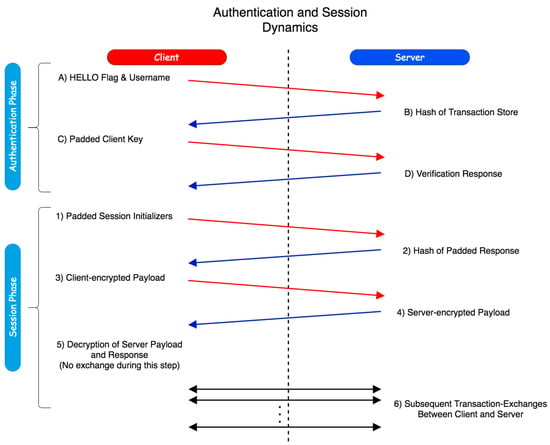
Sensors | Free Full-Text | A Hybrid Dynamic Encryption Scheme for Multi-Factor Verification: A Novel Paradigm for Remote Authentication
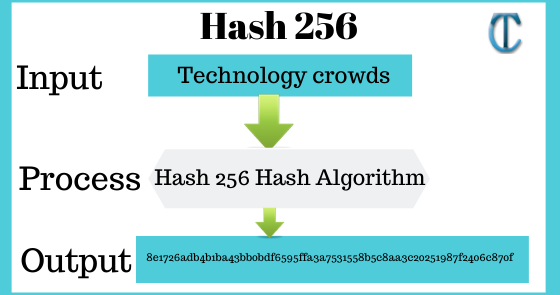
SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds
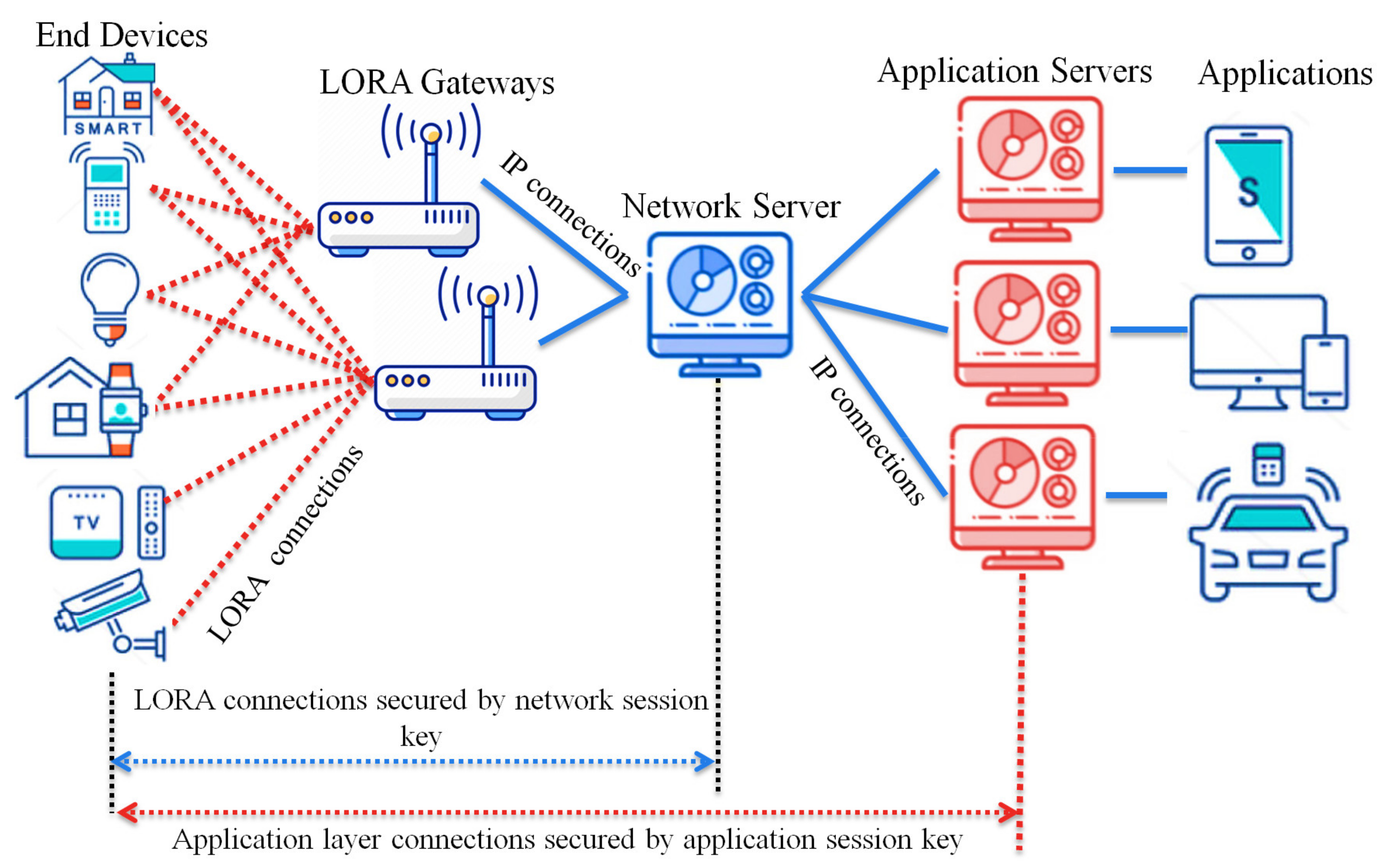
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks
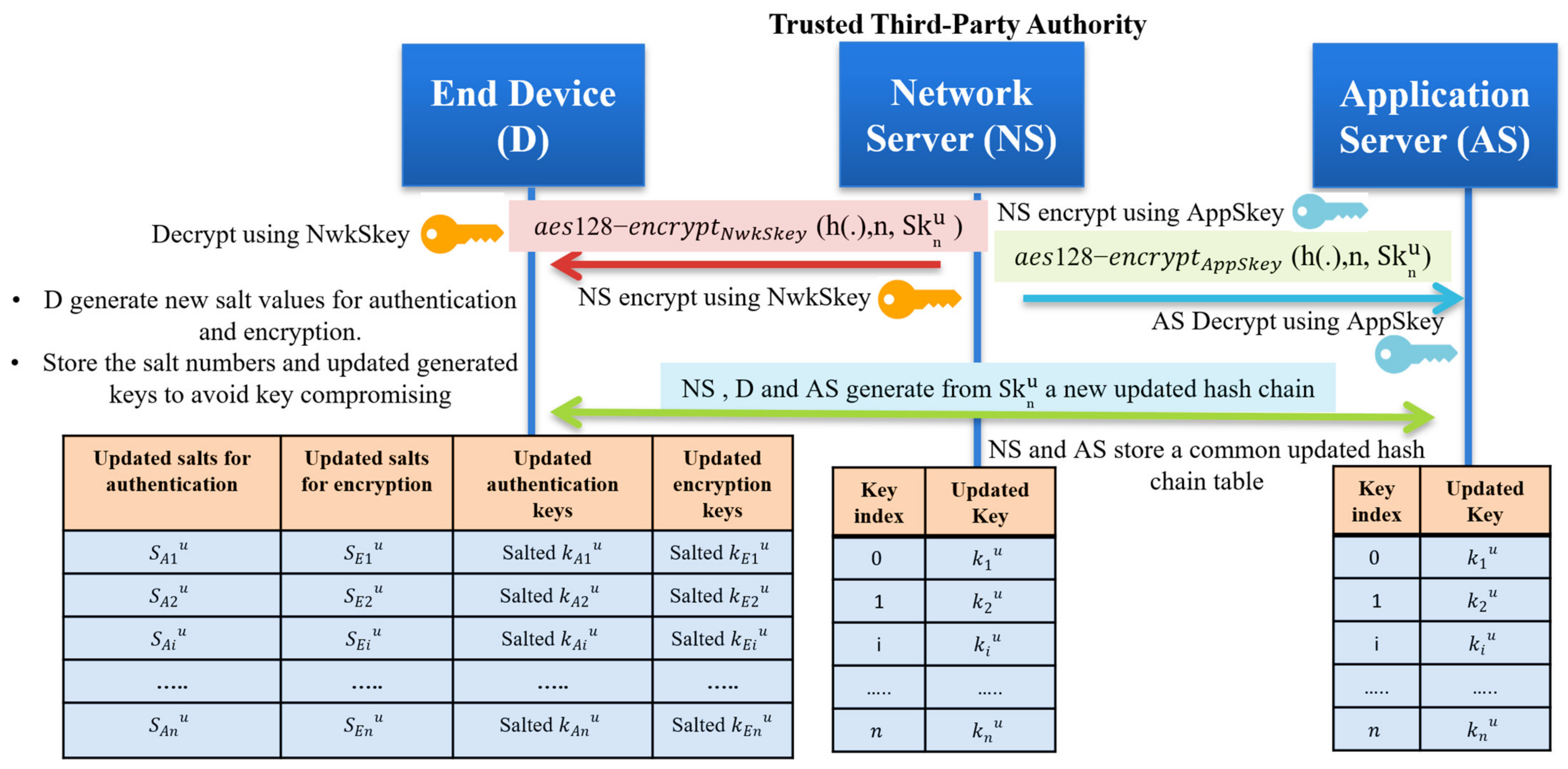
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks
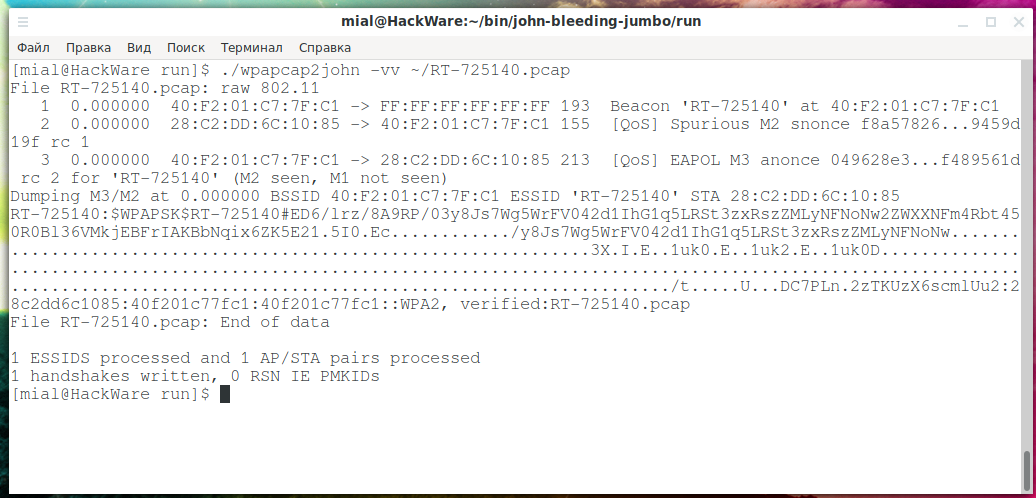
Comprehensive Guide to John the Ripper. Part 2: Utilities for extracting hashes - Ethical hacking and penetration testing