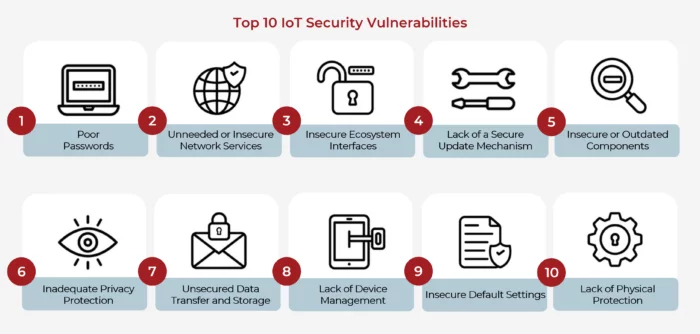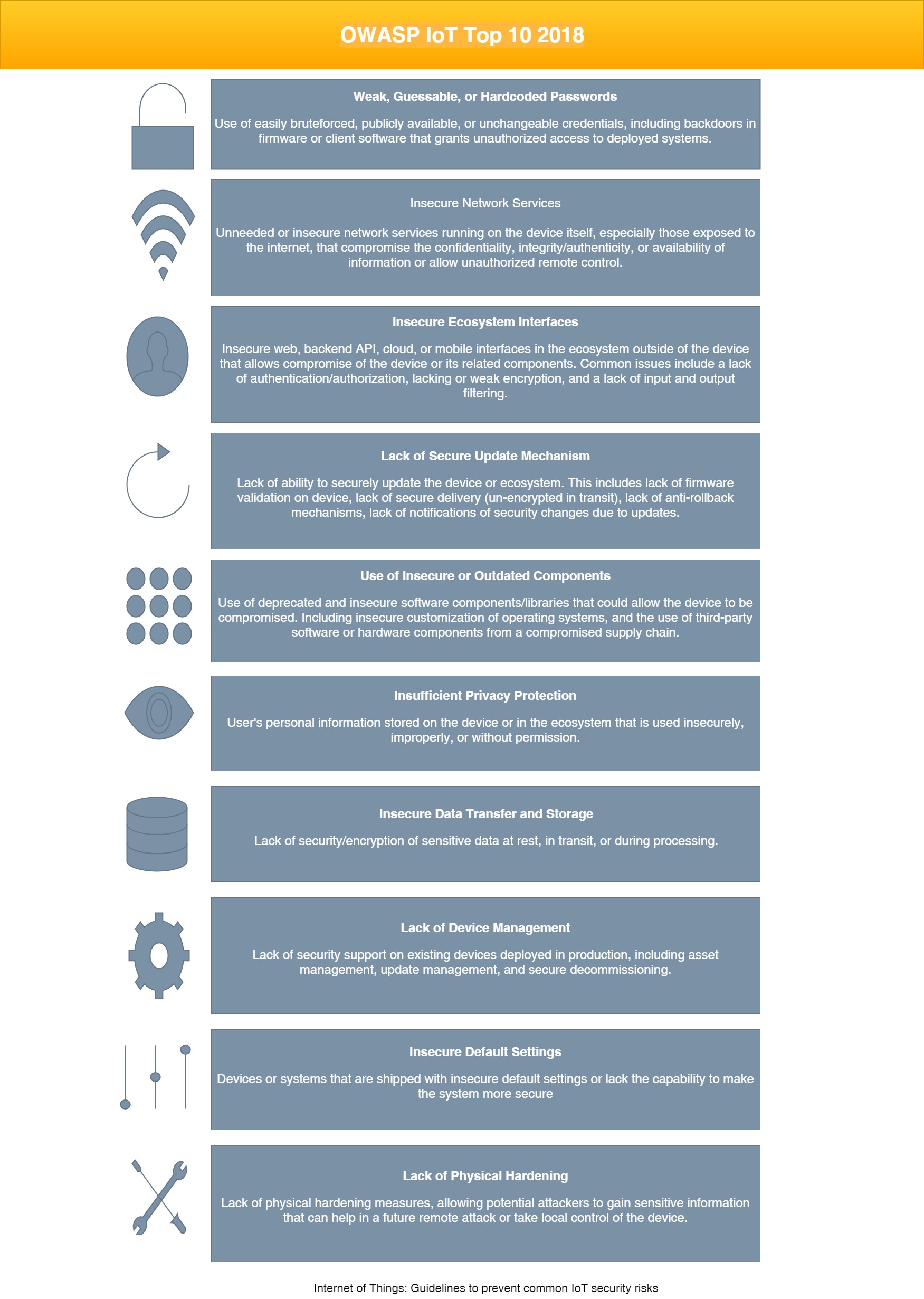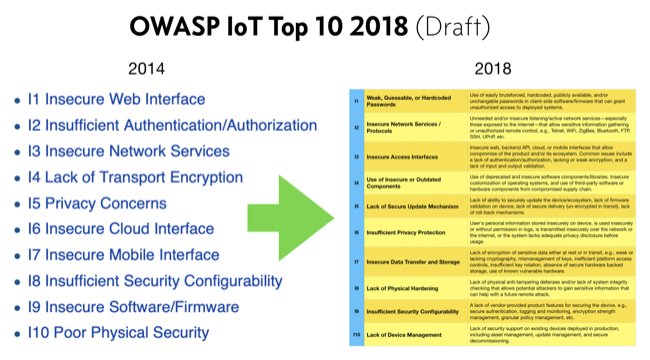
Neira Jones on Twitter: "Preparing to Release the #OWASP #IoT Top 10 2018 https://t.co/cCSmVTmtBB #infosec #appsec #DevSecOps @owasp https://t.co/2WaPcvn4A5" / Twitter
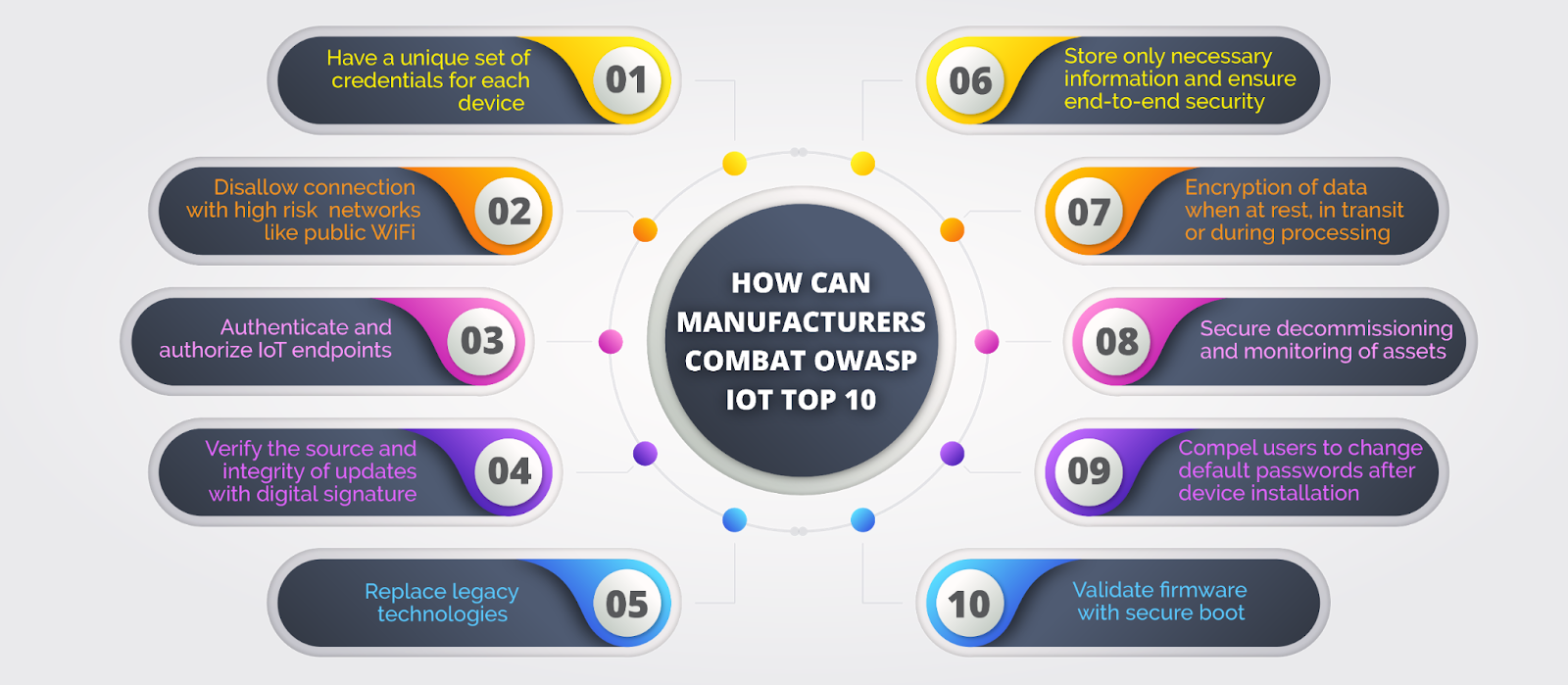
OWASP-IoT-Top-10-2018-Mapping/SUMMARY.md at master · scriptingxss/OWASP-IoT- Top-10-2018-Mapping · GitHub

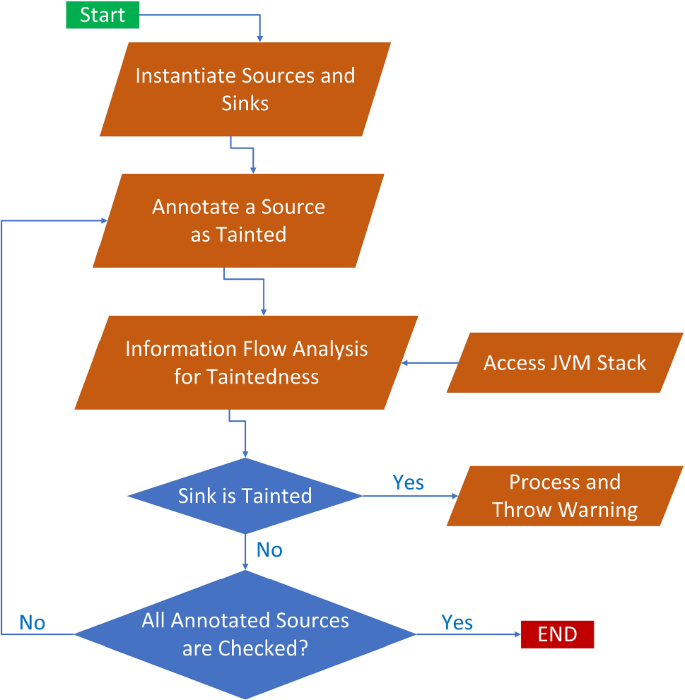
Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks